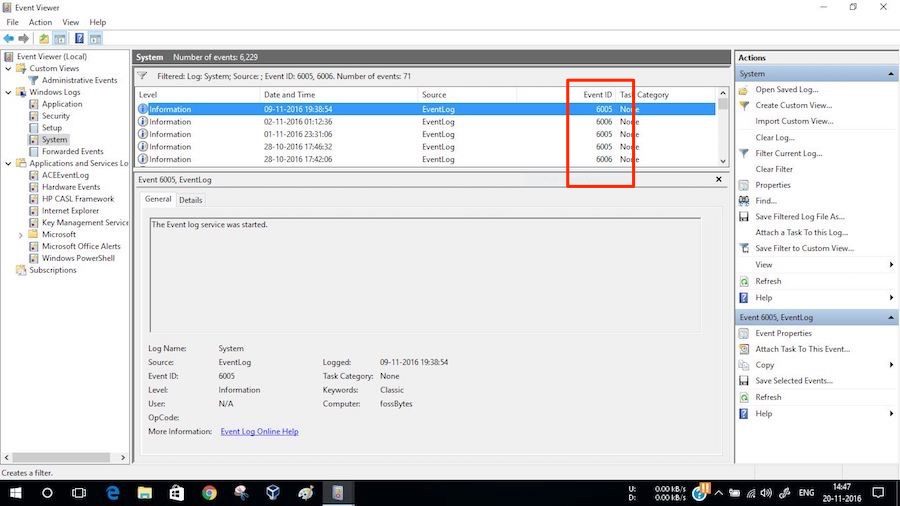
ROHIT CHOUDHARY: TECHMAFIYA brings you a list of the best data recovery software of 2016 which are totally free. These data recovery tools save a lot of hassles after we accidentally delete some important files or we do not take backups before formatting a hard drive. Using these free recovery software, you can recover your data back on your PC.
At this point of time, a data recovery software come in handy. We have compiled a list of best free data recovery software considering factors such as whether the software can recover RAW, Unallocated, Corrupt or Formatted Hard Disk; its ability to recover from different file systems such as FAT, FAT32, HFS, NTFS etc.; the array of devices supported; time taken for file recovery and user friendliness to name a few. Here is a list of-
Top 10 Best Data Recovery Software 2016 for free:
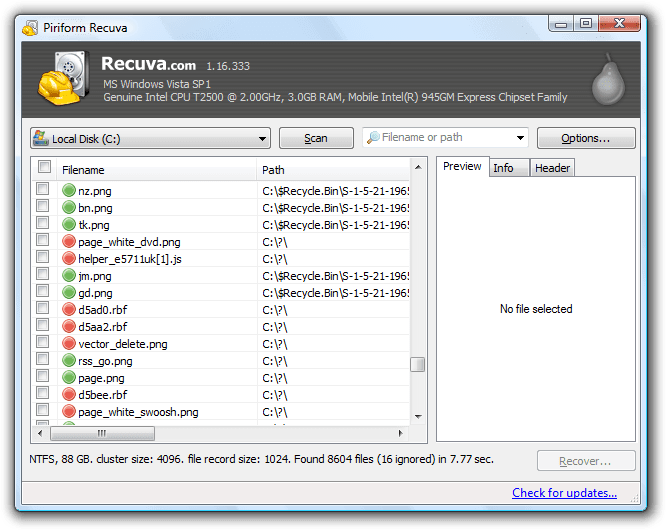
1. Recuva:
The fact that Recuva is on the top of the best data recovery software list, may not come as a surprise to the most of you. Some of the features that bring Recuva on top of the list of Best recovery software are:
- Superior file recovery
- Advanced deep scan mode
- Secure overwrite feature that uses industry & military standard deletion techniques and,
- Ability to recover files from damaged or newly formatted files
- Easy User interface
2. TestDisk:
A list of best data recovery software can hardly be termed as being complete without a mention of TestDisk. Packed with features and a file recovery system that can easily overshadow that of any other data recovery software, TestDisk has a lot to offer for both novices and experts. Here are some of the TestDisk’s features:
- Allows users to recover/rebuild the boot sector
- Fix or recover deleted partition table besides being able to reliably undelete files from FAT, exFAT, NTFS and ext2 file systems.
- Available on all major platforms such as Microsoft Windows, Mac OS X etc and is in fact quite popular as it can be found on various Linux Live CD’s.
Although being a command line tool, TestDisk may not be suitable for some users for data recovery.
3. Undelete 360:
With the looks of a typical Office application, the Undelete 360 is built on a fast yet efficient algorithm which enables the user to undelete files. Here are some of the features of Undelete 360:
- Works on a variety of devices such as Digital cameras, USB’s etc.
- It includes a data-wiping tool, a Hex Viewer along with the ability to preview files before recovery.
- Does a great job in recovering recently deleted files as compared to other free data recovery software
- Also able to recover files of a wide variety of types such as DOC, HTML, AVI, MP3, JPEG, JPG, PNG, GIF, etc.
However, scanning speed needs major improvement and it also lags out its competition in terms of recovering data.
4. PhotoRec:
Definitely one of the best data recovery software out there, PhotoRec is widely acclaimed for its powerful file recovery over a wide variety of devices ranging from digital cameras to hard-disks. Here are some of the features of PhotoRec recovery tool:
- Compatible with almost all major platforms such as Microsoft Windows, Linux, Mac OS X etc.
- Comes packed with the ability to recover more than 440 different file formats.
- Features such as the ‘unformat function’ and the ability to add your own custom file types do come in handy.
Although I wouldn’t advise this free data recovery software to beginners as it is completely devoid of a GUI and uses a command line interface which may intimidate some users.
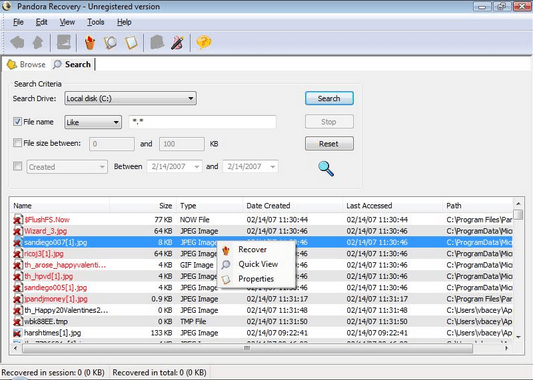
5. Pandora Recovery:
Pandora recovery is one of the most reliable and effective best free data recovery software out there. Pandora recovery tool has a lot to offer to its users. Here are some of the features of this tool:
- Ability to recover deleted files from NTFS and FAT-formatted volumes
- Preview deleted files of certain types (image and text files) without performing recovery
- Surface scan ( which allows you to recover data from drives that have been formatted) and the ability to recover archived, hidden, encrypted and compressed files it packs quite a punch.
- Its interface is very easy to get a hang of and provides an explorer-like view along with color coded & recovery percentage indicators.
However, its file detection system is not that reliable and needs to be improved further. The software could be made portable as well so that it doesn’t consume any space on the hard disk and thereby not consume space that a file which we wish to recover once consumed.
6. MiniTool Partition Recovery:
Standard undelete programs like Recuva, Pandora etc. are perfect for recovering a few deleted files, but what if when you have lost an entire partition? Then you will probably need a specialist application like MiniTool Partition Recovery. Here are some of the great features of this recovery tool specialized in partition recovery:
- An easy wizard-based interface
- Specialized in data recovery on an entire partition
- Point MiniTool Partition Recovery tool at the problematic drive and it will scan for the missing partition.
- Generates a recovery report which will let you know what the program has found to help you in data recovery
- Can’t use data recovery on a bootable disc here.
7. Wise Data Recovery:
Wise data recovery tool is one of the fastest undelete tools among the best data recovery software. Besides being faster, it also comes with some nice features. Here is a list of its features:
- Easy and an intuitive interface
- Can recover deleted files from local drives, USB drives, cameras, memory cards, removable media devices etc.
- Faster search filter by selecting inbuilt file extension groups using the file’s type.
- Compatible from Windows XP to Windows 8.
8. Puran file Recovery:
Puran file recovery works in 3 main recovery modes. These recovery modes are:
- Default Quick Scan (It simply reads the FAT or NTFS file system for deleted files from the recycle bin etc.)
- Deep Scan (includes scanning all available free space) and,
- Full Scan (checks all space on the device for the best chance of recovery)
- Works from Windows XP to Windows 8
Using the “Find lost files” option turns Puran File Recovery into a tool to recover all files from a lost or damaged partition. Something else you can do is edit the custom scan list which stores file signatures for more accurate recovery of badly damaged data.
9. PC Inspector File recovery
PC Inspector File Recovery Works well on both FAT and NTFS drive even if the boot sector has been erased or damaged. Here are some of the features of this recovery tool.
- Simple search dialog can help locate files by name.
- Recovered files can be restored to a local hard disk or network drives.
- Can recover image and video of several types of files in different formats such as ARJ, AVI, BMP, DOC, DXF, XLS, EXE, GIF, HLP, HTML, JPG, LZH, MID, MOV, MP3, PDF, PNG, RTF, TAR, TIF, WAV and ZIP.
- Can scan just specific areas of the disc with the Cluster scanner
- Works perfectly from Windows XP to Windows 7
However, the interface is a little confusing mess of tabs. So, be careful with this tool.
10. Restoration
Restoration data recovery program takes the final position in the list of top 10 best data recovery tools. It is no different and is similar to the other free undelete apps on this list. Even if it is in the tenth position, here are a few things that we liked about this data recovery tool:
- Very simple and easy to use
- No confusing and no cryptic buttons or any complicated file recovery procedures
- It can recover data and files from hard drives, memory cards, USB drives, and other external drives as well.
- Does not need to be installed and can run data recovery from a floppy disk or USB drive.
- Supports Windows Vista, XP, 2000, NT, ME, 98, and 95 and also, successfully tested Windows 7 and Windows 10.
- Sometimes, runs into a problem with Windows 8
Bonus File Recovery Software:
11. Stellar Data Recovery
Living up to its name, Stellar Data Recovery performs a stellar job in recovering your data from your Windows PC and Mac. If you are regretting your decision of deleting recent files, Stellar Data Recovery tool is here to help you in an effective way. This risk-free program recovers data from different types of storage devices like memory cards, smartphones, USB drives, hard disks etc.
Using Stellar Data Recovery program is simple. Just download it, start the scan, and you are able to recover from the past data disasters. If you are willing to give it a try, here’s the download page.
Editor’s pick:
I would personally recommend Piriform’s Recuva to all our readers, hands down. With superior file recovery , an advanced deep scan mode, a secure overwrite feature that uses industry & military standard deletion techniques and the ability to recover files from damaged or newly formatted files , Recuva is undeniably one of the best free data recovery tools out there. Its portability (the ability to run without installation) is one feature that sets it apart from the others.
The User Interface wouldn’t let you down either with a file-recovery wizard and an application manual mode available to your disposal which provides color coding (indicating the probability of the recovery of a file) along with the ability to preview files before undeleting them. Recuva is definitely a notch above all others and undoubtedly the most complete and reliable free data recovery software available today.